FC2 & Rakuten Online Websites Multiple XSS (Cross-site Scripting) and Open Redirect Cyber Vulnerabilities
FC2 and Rakuten are the first and second top ranking Japanese local online websites. This article introduces several XSS (Cross-site Scripting) and Open Redirect bugs of them.
The Alexa rank of fc2.com is 52 on February 18 2015 and related rank in Japan is 4. The Alexa rank of rakuten.co.jp is 64 on May 29 2015 and related rank is japan is 7. We know that Google, Facebook, Twitter, Yahoo, Microsoft, Apple and LinkedIn are not local Japanese companies at all.
Discover and Reporter:
Wang Jing, Division of Mathematical Sciences (MAS), School of Physical and Mathematical Sciences (SPMS), Nanyang Technological University (NTU), Singapore. (@justqdjing)
http://www.tetraph.com/wangjing
(1) FC2 XSS (cross site scripting) & Open Redirect
“FC2 (founded July 20, 1999) is a popular Japanese blogging host, the third most popular video hosting service in Japan (after YouTube and Niconico), and a web hosting company headquartered in Las Vegas, Nevada. It is the sixth most popular website in Japan overall (as of January 2014). FC2 is an abbreviation of “Fantastic Kupi-Kupi (クピクピ)”. It is known to allow controversial adult content such as pornography and hate speech (unlike many of its competitors). The company uses rented office space for its headquarters which it shares with many other U.S.-based businesses. It also pays taxes in the United States. The physical servers are located in the United States. However, it is believed that the majority of the company and its users (including employees) are located within Japan” (Wikipedia)
The Alexa rank of fc2.com is 52 on February 18 2015. It is the toppest Japanese local website sevice.
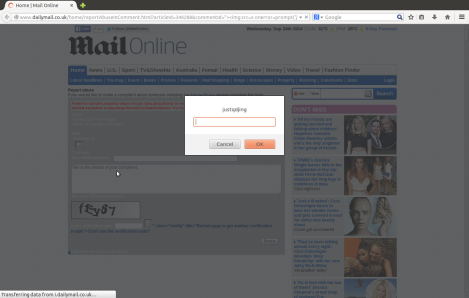
(1.1) FC2 fc2.com Online Website URLs XSS (cross site scripting) Vulnerabilities (All URLs Under Domain blog.fc2.com/tag)
Vulnerability description:
FC2 has a computer cyber security bug problem. It is vulnerable to XSS attacks. Here is the description of XSS: “Hackers are constantly experimenting with a wide repertoire of hacking techniques to compromise websites and web applications and make off with a treasure trove of sensitive data including credit card numbers, social security numbers and even medical records. Cross-site Scripting (also known as XSS or CSS) is generally believed to be one of the most common application layer hacking techniques Cross-site Scripting allows an attacker to embed malicious JavaScript, VBScript, ActiveX, HTML, or Flash into a vulnerable dynamic page to fool the user, executing the script on his machine in order to gather data. The use of XSS might compromise private information, manipulate or steal cookies, create requests that can be mistaken for those of a valid user, or execute malicious code on the end-user systems. The data is usually formatted as a hyperlink containing malicious content and which is distributed over any possible means on the internet.” (Acunetix)

The vulnerability can be attacked without user login. Tests were performed on Firefox (37.02) in Ubuntu (14.04) and IE (9.0.15) in Windows 7.
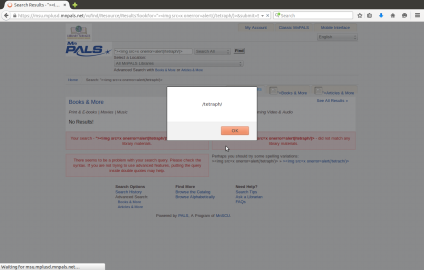
(1.2) FC2 Online Web Service Open Redirect (Unvalidated Redirects and Forwards) Cyber Security Vulnerabilities
(1.2.1) Vulnerability Description:
FC2 online web service has a computer cyber security bug problem. It can be exploited by Open Redirect (Unvalidated Redirects and Forwards) attacks. Here is the description of Open Redirect: “An open redirect is an application that takes a parameter and redirects a user to the parameter value without any validation. This vulnerability is used in phishing attacks to get users to visit malicious sites without realizing it.” One consequences of it is Phishing. (OWASP)
The program code flaw can be attacked without user login. Tests were performed on Microsoft IE (9 9.0.8112.16421) of Windows 7, Mozilla Firefox (37.0.2) & Google Chromium 42.0.2311 (64-bit) of Ubuntu (14.04.2),Apple Safari 6.1.6 of Mac OS X v10.9 Mavericks.
In fact, during the test, it is not hard to find URL Redirection bugs in FC2. Maybe fc2.com pays little attention to mitigate these Vulnerabilities. These bugs were found by using URFDS.
(1.3) Vulnerability Disclosure:
Those vulnerabilities were reported to rakuten-cert@rakuten.co.jp in 2014. No one replied. Until now, they are still unpatched.
(2) Rakuten XSS (cross site scripting) & Open Redirect
“Rakuten, Inc. (楽天株式会社 Rakuten Kabushiki-gaisha?) is a Japanese electronic commerce and Internet company based in Tokyo, Japan. Its B2B2C e-commerce platform Rakuten Ichiba is the largest e-commerce site in Japan and among the world’s largest by sales. Hiroshi Mikitani founded the company in February 1997 as MDM, Inc., and is still its chief executive. Rakuten Shopping Mall (楽天市場 Rakuten Ichiba?) started operations in May 1997. In June 1999, the company changed its name to Rakuten, Inc. The Japanese word rakuten means optimism. In 2012, the company’s revenues totaled US$4.6 billion with operating profits of about US$244 million. In June 2013, Rakuten, Inc. reported it had a total of 10,351 employees worldwide. In 2005, Rakuten started expanding outside Japan, mainly through acquisitions and joint ventures. Its acquisitions include Buy.com (now Rakuten.com Shopping in the US), Priceminister (France), Ikeda (now Rakuten Brasil), Tradoria (now Rakuten Deutschland), Play.com (UK), Wuaki.tv (Spain), and Kobo Inc. (Canada). The company has investments in Pinterest, Ozon.ru, AHA Life, and Daily Grommet.” (Wikipedia)
The Alexa rank of rakuten.co.jp is 64 in May 29 2015. It is the second toppest Japanese local sevice website.
(2.1) Rakuten Website Search Page XSS (cross site scripting) Web Security Vulnerability
(2.1.1) Vulnerability description:
rakuten.de has a computer science security bug problem. It is vulnerable to XSS attacks. Here is the description of XSS: “Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted web sites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a IEEE web application uses input from a user within the output it generates without validating or encoding it.” (OWSAP)
The vulnerability can be attacked without user login. Tests were performed on Firefox (37.02) in Ubuntu (14.04) and IE (8.0. 7601) in Windows 7. The bugs found by using CSXDS.
(2.1.3) Vulnerability Disclosure:
Those vulnerabilities are patched now.
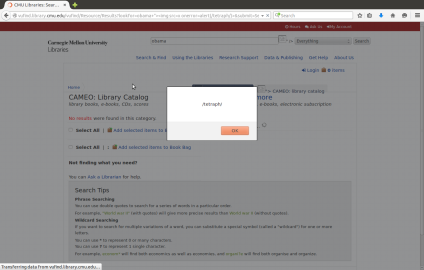
(2.2) Rakuten Online Website Open Redirect (URL Redirection) Cyber Security Vulnerabilities
(2.2.1) Vulnerability Description:
Rakuten online website has a computer engineering security bug problem. It can be exploited by URL Redirection (Unvalidated Redirects and Forwards) attacks. Here is the description of Open Redirect: “A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect. This simplifies phishing attacks. An http parameter may contain a URL value and could cause the web application to redirect the request to the specified URL. By modifying the URL value to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials. Because the server name in the modified link is identical to the original site, phishing attempts have a more trustworthy appearance.” (From CWE)
“The Full Disclosure mailing list is a public forum for detailed discussion of vulnerabilities and exploitation techniques, as well as tools, papers, news, and events of interest to the community. FD differs from other security lists in its open nature and support for researchers’ right to decide how to disclose their own discovered bugs. The full disclosure movement has been credited with forcing vendors to better secure their products and to publicly acknowledge and fix flaws rather than hide them. Vendor legal intimidation and censorship attempts are not tolerated here!” A great many of the fllowing web securities have been published here, Buffer overflow, HTTP Response Splitting (CRLF), CMD Injection, SQL injection, Phishing, Cross-site scripting, CSRF, Cyber-attack, Unvalidated Redirects and Forwards, Information Leakage, Denial of Service, File Inclusion, Weak Encryption, Privilege Escalation, Directory Traversal, HTML Injection, Spam.
The program code flaw can be attacked without user login. Tests were performed on Microsoft IE (9 9.0.8112.16421) of Windows 7, Mozilla Firefox (37.0.2) & Google Chromium 42.0.2311 (64-bit) of Ubuntu (14.04.2),Apple Safari 6.1.6 of Mac OS X v10.9 Mavericks.
Since know only a little Japanese, not sure whether Rakuten pays much attention to Open Redirect Vulnerabilities or not.
(2.2.3) Vulnerability Disclosure:
Those vulnerabilities are not patched now.
FC2&楽天オンラインのウェブサイトの複数のXSS(クロスサイトスクリプティング)とオープンリダイレクトサイバー脆弱性
FC2と楽天は日本の地方オンラインWebサービスをランク付けする第一及び第二toppestです。この記事では、いくつかのXSS(クロスサイトスクリプティング)とオープンリダイレクトのバグを紹介します。
fc2.comのAlexaのランクは2015年2月18日に52であり、日本のランクはrakuten.co.jpのAlexaのランクは2015年5月29日に64で4であるとランク、日本は7です。
(1)FC2 XSS(クロスサイトスクリプティング)&オープンリダイレクト
(1999年7月20日に設立)」FC2は、日本の人気ブログのホスト、(YouTubeやニコニコ後)は、日本で3番目に人気のビデオホスティングサービス、およびラスベガス、ネバダ州に本社を置くウェブホスティング会社です。それは第六最も人気のあります全体的な日本のウェブサイト(2014年1月現在)。FC2はの略で、「ファンタスティックKupi-Kupi(クピクピ)」。これは、このようなポルノのような論争のアダルトコンテンツを許可することが知られており、(競合他社の多くとは異なり)スピーチを嫌いされています。会社それは他の多くの米国系企業と共有し、その本社のためのオフィススペースを借り使用しています。また、米国で税金を払っています。物理サーバが米国に所在している。しかし、それは会社の大部分と考えられ、そのされていますユーザー(従業員を含む)は、日本の中に位置しています」(ウィキペディア)
fc2.comのAlexaのランクはそれがtoppest日本のローカルウェブサイトの流通サービスである2月18日2015年に52です。
(1.1)FC2 fc2.comオンラインのウェブサイトのURL XSS(クロスサイトスクリプティング)脆弱性(ドメインblog.fc2.com/tag下にあるすべてのURL)
FC2は、コンピュータのサイバーセキュリティバグの問題があります。これは、XSS攻撃に対して脆弱です。ここでXSSの説明は次のとおりです。「ハッカーは常にWebサイトやWebアプリケーションを侵害し、クレジットカード番号、社会保障番号、さらには医療記録などの機密データの宝庫でオフにする技術をハッキングの幅広いレパートリーで実験されている4クロス。サイトスクリプティングは、(また、XSSやCSSとして知られる)は、一般のVBScript、ActiveXの、HTML、またはFlashはに対して脆弱動的ページに、攻撃者が悪意のあるJavaScriptを埋め込むことができ、最も一般的なアプリケーション層ハッキング技術クロスサイトスクリプティングの一つであると考えられていますデータを収集するために、自分のマシン上でスクリプトを実行して、ユーザーをだます。XSSの使用が有効なユーザーの方に誤解されるか、または最後に悪質なコードを実行できる要求を作成し、操作したり、クッキーを盗む、個人情報を危険にさらす可能性があります-userシステムでは、データは通常、悪質なコンテンツを含むハイパーリンクとしてフォーマットされ、インターネット上の任意の可能な手段を介して配布されています。」 (会社のAcunetix)
この脆弱性は、ユーザのログインなしで攻撃される可能性があります。試験は、Windows 7でのUbuntuでのFirefox(37.02)(14.04)およびIE(9.0.15)で行いました。
(1.2)FC2オンラインWebサービスのオープンリダイレクト(未検証のリダイレクトとフォワード)サイバー·セキュリティの脆弱性
FC2オンラインWebサービスは、コンピュータのサイバーセキュリティバグの問題があります。それは、オープンリダイレクト(未検証のリダイレクトとフォワード)攻撃によって悪用される可能性があります。ここでオープンリダイレクトの説明は次のとおりです。「オープンリダイレクトがパラメータを受け取り、何の検証も行わずにパラメータ値にユーザーをリダイレクトするアプリケーションです。この脆弱性は、それを実現することなく、悪質なサイトを訪問するユーザーを取得するためにフィッシング攻撃で使用されています。。 “それの一つの結果はフィッシングです。 (OWASP)
プログラムコードの欠陥は、ユーザのログインなしで攻撃される可能性があります。テストは、Windows 7のMicrosoftのIE(9 9.0.8112.16421)で行われた、Mozilla Firefoxの(37.0.2)&グーグルクロム42.0.2311のUbuntuの(64ビット)(14.04.2)はMac OSのアップルのSafari 6.1.6 X v10.9マーベリックス。
実際には、テスト時には、FC2内のURLリダイレクトのバグを見つけることは難しいことではありません。多分fc2.comは、これらの脆弱性を軽減するためにはほとんど注意を払っています。これらのバグはURFDSによって発見されました。
これらの脆弱性は誰も答えていない2014年にrakuten-cert@rakuten.co.jpすることが報告されました。今までは、彼らはまだパッチを適用していないです。
(2)楽天XSS(クロスサイトスクリプティング)&オープンリダイレクト
「楽天株式会社は、(楽天株式会社楽天株式会社-gaisha?)東京、日本に拠点を置く日本の電子商取引やインターネット企業です。そのB2B2Cの電子商取引プラットフォーム楽天市場は、日本最大の電子商取引サイトで、世界の中で販売による最大。三木谷浩史は、MDM、株式会社として1997年2月で会社を設立し、さらにその最高経営責任者(CEO)である。楽天ショッピングモール(楽天市場楽天市場?)1999年6月1997年5月で事業を開始し、同社は社名変更楽天株式会社に日本語ワード楽天楽観を意味している。2012年には、同社の売上高は、米国約US2.44億ドルの営業利益との46億ドルとなりました。2013年6月には、楽天株式会社は、それが世界中の10351名の従業員を有していたと報告した。で2005年、楽天は、主に買収や合弁事業を通じて、日本国外で拡大し始めた。その買収は、Buy.com(米国で今Rakuten.comショッピング)、Priceminister(フランス)、池田(現楽天ブラジル)、Tradoria(今楽天ドイツ)が挙げられます、Play.com(英国)、Wuaki.tv(スペイン)、およびコボ(カナダ)。同社はPinterest、Ozon.ru、AHA生活、毎日のグロメットで投資を行っている。」(ウィキペディア)
rakuten.co.jpのAlexaのランクは、第2 toppest日本の地方流通サービスのウェブサイトである5月29日2015年64あります。
(2.1)楽天ウェブ検索ページXSS(クロスサイトスクリプティング)のWebセキュリティ脆弱性
rakuten.deは、コンピュータのサイバーセキュリティバグの問題があります。これは、XSS攻撃に対して脆弱です。ここでXSSの説明です:「クロスサイトスクリプティング(XSS)攻撃は、悪意のあるスクリプトがそうでなければ良性と信頼できるWebサイトに注入された注入の種類、ある攻撃者が悪意のあるコードを送信するために、Webアプリケーションを使用する際にXSS攻撃が発生しました。 、一般的にブラウザ側スクリプトの形で、別のエンドユーザーに。これらの攻撃が成功することを可能に傷はかなり普及しているWebアプリケーションはそれを検証するか、エンコードせずに生成する出力内のユーザからの入力を使用して任意の場所に発生します。」 (OWSAP)
この脆弱性は、ユーザのログインなしで攻撃される可能性があります。テストはWindows 7でのUbuntu(14.04)とIE(8.0。7601)にはFirefox(37.02)で行いました。
(2.2)楽天オンラインサイトオープンリダイレクト(URLリダイレクション)サイバー·セキュリティの脆弱性
楽天のオンラインウェブサイトは、コンピュータのサイバーセキュリティバグの問題があります。それは、オープンリダイレクト(未検証のリダイレクトとフォワード)攻撃によって悪用される可能性があります。ここでオープンリダイレクトの説明は次のとおりです。「Webアプリケーションは外部サイトへのリンクを指定するユーザ制御入力を受け付け、リダイレクトでそのリンクを使用しています。これは、フィッシング攻撃を簡素化HTTPパラメータがURL値が含まれており、可能性があります。。指定されたURLに要求をリダイレクトするようにWebアプリケーションを引き起こす。悪質なサイトへのURLの値を変更することにより、攻撃者がフィッシング詐欺を起動し、ユーザーの資格情報を盗むことができる。変更されたリンク内のサーバー名が、元のサイトと同じであるため、フィッシングの試みは、より信頼性の高い外観を持っています。」 (CWEから)
「完全な情報開示のメーリングリストは脆弱性と搾取の技術だけでなく、ツール、論文、ニュース、コミュニティに関心のあるイベントの詳細な議論のための公開フォーラムです。FDは、研究者のためのオープンな性質とサポートで他のセキュリティ·リストとは異なり「右はより自分の製品を確保するためにベンダーを強制し、公に認め、それらを隠すのではなく、欠陥を修正するために完全な情報開示の動きが入金されている。自分の発見したバグを開示する方法を決定する法的脅迫や検閲の試みをベンダーここでは許容されないために! ” fllowingウェブ証券の非常に多くがここで公開されている、バッファオーバーフロー、HTTPレスポンス分割(CRLF)、CMDインジェクション、SQLインジェクション、フィッシング、クロスサイトスクリプティング、CSRF、サイバー攻撃、未検証のリダイレクトとフォワード、情報漏洩、サービス、ファイルインクルージョン、弱い暗号化、権限昇格、ディレクトリ·トラバーサル、HTMLインジェクション、スパム拒否。
プログラムコードの欠陥は、ユーザのログインなしで攻撃される可能性があります。テストは、Windows 7のMicrosoftのIE(9 9.0.8112.16421)で行われた、Mozilla Firefoxの(37.0.2)&グーグルクロム42.0.2311のUbuntuの(64ビット)(14.04.2)はMac OSのアップルのSafari 6.1.6 X v10.9マーベリックス。
楽天リダイレクトの脆弱性かどうかを開くために多くの注意を払っているかどうかわからない、少しだけ日本語を知っているので。
これらの脆弱性は、現在パッチが適用されていません。