Daily mail Registration Page Unvalidated Redirects and Forwards & XSS Web Security Problem
Website Description:
“The Daily Mail is a British daily middle-market tabloid newspaper owned by the Daily Mail and General Trust. First published in 1896 by Lord Northcliffe, it is the United Kingdom’s second biggest-selling daily newspaper after The Sun. Its sister paper The Mail on Sunday was launched in 1982. Scottish and Irish editions of the daily paper were launched in 1947 and 2006 respectively. The Daily Mail was Britain’s first daily newspaper aimed at the newly-literate “lower-middle class market resulting from mass education, combining a low retail price with plenty of competitions, prizes and promotional gimmicks”, and was the first British paper to sell a million copies a day. It was at the outset a newspaper for women, the first to provide features especially for them, and as of the second-half of 2013 had a 54.77% female readership, the only British newspaper whose female readers constitute more than 50% of its demographic. It had an average daily circulation of 1,708,006 copies in March 2014. Between July and December 2013 it had an average daily readership of approximately 3.951 million, of whom approximately 2.503 million were in the ABC1 demographic and 1.448 million in the C2DE demographic. Its website has more than 100 million unique visitors per month.” (Wikipedia)
One of its website’s Alexa rank is 93 on January 01 2015. The website is one of the most popular websites in the United Kingdom.
The Unvalidated Redirects and Forwards problem has not been patched, while the XSS problem has been patched.
(1) Daily mail Registration Page Unvalidated Redirects and Forwards Web Security Problem
(1.1) Vulnerability Description:
Daily online websites have a cyber security problem. Hacker can exploit it by Open Redirect (Unvalidated Redirects and Forwards) attacks. During the tests, all Daily mail websites (Daily Mail, Mail on Sunday & Metro media group) use the same mechanism. These websites include dailymail.co.uk, thisismoney.co.uk, and mailonsunday.co.uk.
Google Dork:
“Part of the Daily Mail, The Mail on Sunday & Metro Media Group”
The vulnerability occurs at “&targetUrl” parameter in “logout.html?” page, i.e.
http://www.dailymail.co.uk/registration/logout.html?targetUrl=http%3A%2F%2Fgoogle.com
(1.2.1) Use the following tests to illustrate the scenario painted above.
The redirected webpage address is “http://diebiyi.com/articles“. Can suppose that this webpage is malicious.
Vulnerable URLs:
http://www.dailymail.co.uk/registration/logout.html?targetUrl=http%3A%2F%2Fdailymail.co.uk
http://www.thisismoney.co.uk/registration/logout.html?targetUrl=http%3A%2F%2Fhao123.com/
http://www.mailonsunday.co.uk/registration/logout.html?targetUrl=http%3A%2F%2Fpinterest.com
POC Code:
http://www.dailymail.co.uk/registration/logout.html?targetUrl=http%3A%2F%2Fdiebiyi.com/articles
http://www.thisismoney.co.uk/registration/logout.html?targetUrl=http%3A%2F%2Fdiebiyi.com/articles
http://www.mailonsunday.co.uk/registration/logout.html?targetUrl=http%3A%2F%2Fdiebiyi.com/articles
Blog Details:
http://tetraph.com/security/website-test/daily-mail-url-redirection/
http://securityrelated.blogspot.com/2015/10/daily-mail-registration-page.html
(1.2.2) The program code flaw can be attacked without user login. Tests were performed on Microsoft IE (9 9.0.8112.16421) of Windows 8, Mozilla Firefox (37.0.2) & Google Chromium 42.0.2311 (64-bit) of Ubuntu (14.04.2),and Apple Safari 6.1.6 of Mac OS X v10.9 Mavericks.
These bugs were found by using URFDS (Unvalidated Redirects and Forwards Detection System).
(1.2) Description of Open Redirect:
Here is the description of Open Redirect: “A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect. This simplifies phishing attacks. An http parameter may contain a URL value and could cause the web application to redirect the request to the specified URL. By modifying the URL value to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials. Because the server name in the modified link is identical to the original site, phishing attempts have a more trustworthy appearance.” (From CWE)
(1.3) Vulnerability Disclosure:
These vulnerabilities have not been patched.
(2) Daily Mail Website XSS Cyber Security Zero-Day Vulnerability
(2.1) Vulnerability description:
DailyMail has a security problem. Criminals can exploit it by XSS attacks.
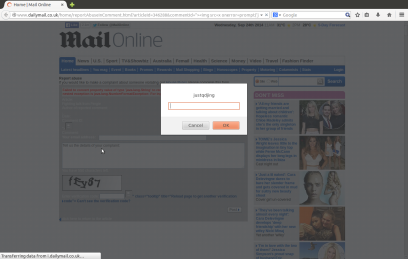
The vulnerability occurs at “reportAbuseInComment.html?” page with “&commentId” parameter, i.e.
http://www.dailymail.co.uk/home/reportAbuseInComment.html?articleId=346288&commentId=877038
POC Code:
http://www.dailymail.co.uk/home/reportAbuseInComment.html?articleId=346288&commentId=”><img src=x onerror=prompt(‘justqdjing’)>
The vulnerability can be attacked without user login. Tests were performed on Mozilla Firefox (34.0) in Ubuntu (14.04) and Microsoft IE (9.0.15) in Windows 7.
Poc Video:
https://www.youtube.com/watch?v=Oig-ZrlJDf8&feature=youtu.be
Blog Detail:
http://tetraph.com/security/web-security/daily-mail-xss-bug/
http://securityrelated.blogspot.com/2015/10/daily-mail-online-website-xss-cyber.html
(2.2) What is XSS?
“Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side script into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy. Cross-site scripting carried out on websites accounted for roughly 84% of all security vulnerabilities documented by Symantec as of 2007. Their effect may range from a petty nuisance to a significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site’s owner.” (Wikipedia)
(2.3) Vulnerability Disclosure:
This vulnerability has been patched.
Blog Details:
http://tetraph.com/security/website-test/daily-mail-open-redirect-xss/
http://securityrelated.blogspot.com/2015/10/daily-mail-url-redirection-and-xss-bug.html
https://vulnerabilitypost.wordpress.com/2015/10/30/daily-mail-url-redirect-xss/
Discover and Reporter:
Wang Jing, Division of Mathematical Sciences (MAS), School of Physical and Mathematical Sciences (SPMS), Nanyang Technological University (NTU), Singapore. (@justqdjing)
http://www.tetraph.com/wangjing
Reference:
http://permalink.gmane.org/gmane.comp.security.fulldisclosure/2643
http://lists.openwall.net/full-disclosure/2015/11/03/8
https://infoswift.wordpress.com/2015/11/02/daily-mail-xss/
http://frenchairing.blogspot.com/2015/11/daily-mail-xss-bug.html
https://cxsecurity.com/issue/WLB-2015110028
https://www.mail-archive.com/fulldisclosure%40seclists.org/msg02683.html
https://progressive-comp.com/?l=full-disclosure&m=144651836427184&w=1
http://whitehatpost.lofter.com/post/1cc773c8_8d458d1
http://ithut.tumblr.com/post/132724992778/daily-mail-xss
https://biyiniao.wordpress.com/2015/11/03/daily-mail-xss/
http://seclists.org/fulldisclosure/2015/Nov/7
http://japanbroad.blogspot.com/2015/11/daily-mail-xss.html